aws-marketplace-addon-kong-gateway
Kong Gateway EKS AddOn from AWS Marketplace
This document shows the steps required to use EKS AddOn from AWS Marketplace
Pre-Requisites
- Amazon Elastic Kubernetes Service (EKS) Cluster. See the userguide here
- A valid Kong Konnect subscription. You can subscribe to Kong Konnect from AWS Marketplace. See details here
- Subscribe to Kong Konnect Dataplane - EKS Add On
- Generate the certificate and save as Kubernetes Secrets
4.1 Login to Kong Konnect, and navigate to Gateway Manager to create a new Control plane to add new self managed dataplane nodes (hybrid) and pinned certificate. Alternatively, if you want to connect the data plane nodes to an existing control plane then navigate to Data Plane Certificates
4.2 Since we’re going to deploy our Data Plane with Runtime Instance on Amazon EKS, click on Kubernetes.
4.3 Navigate to the cli, and create a k8s namespace, kong for the Data Plane
kubectl create namespace kong
4.4 Generate the certificates Konnect requires through the UI, by clicking Generate Certificate
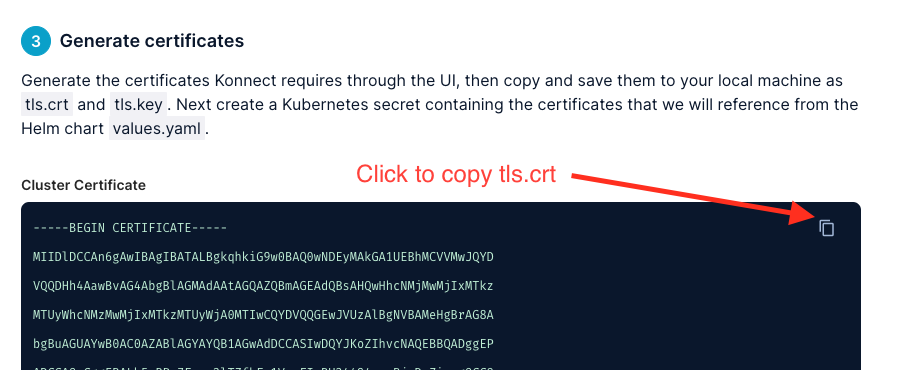
4.5 Copy the generated Cluster Certificate from Kong UI and paste them into the environment where you will run kubectl commands in a file named tls.crt
cat >> tls.crt << EoF
PASTE_THE_CONTENTS_OF_COPIED_CODE
EoF
Don’t forget to replace PASTE_THE_CONTENTS_OF_COPIED_CODE in the above command with the copied code from the Kong UI
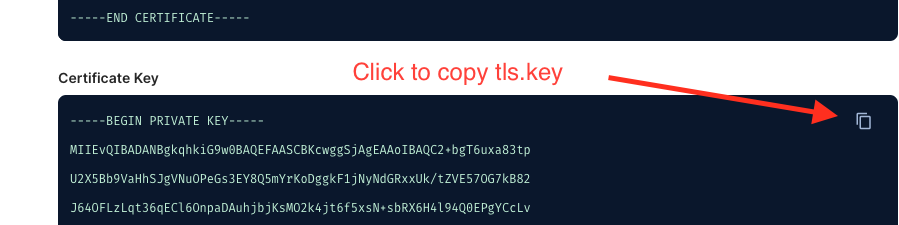
4.6 Then copy the generated Certificate Key from Kong UI and paste them to your cloudshell environment in a file named tls.key
cat >> tls.key << EoF
PASTE_THE_CONTENTS_OF_COPIED_CODE
EoF
4.7 Create Kubernetes Secret
kubectl create secret tls kong-cluster-cert -n kong --cert=./tls.crt --key=./tls.key
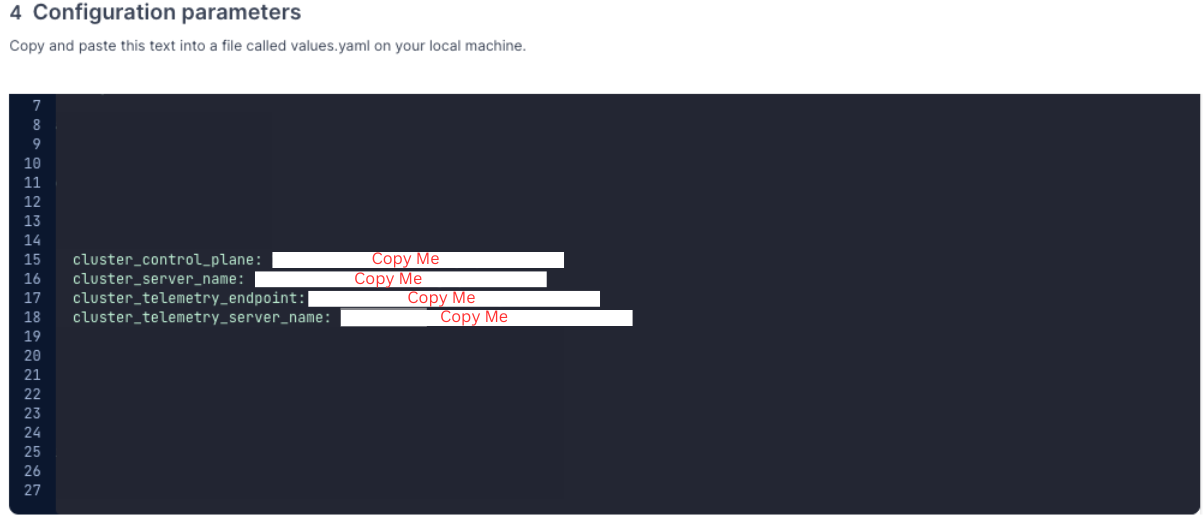
4.8 Under Configuration Parameters Section, copy/note down the following attributes :
cluster_control_planecluster_server_namecluster_telemetry_endpointcluster_telemetry_server_name
You won’t need to note any other values from this section.
Close the window (Done).
Provision Kong Gateway EKS AddOn via AWS console
These steps will be executed in the AWS Console.
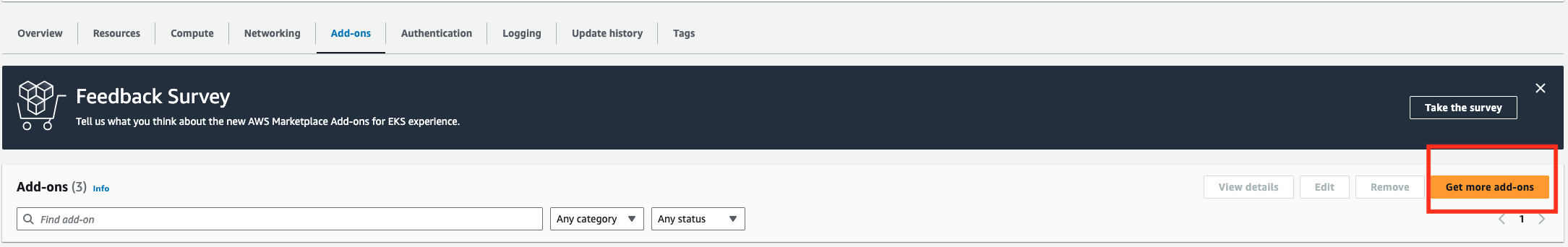
- Navigate to the EKS Cluster > Add-Ons > Get More add-ons
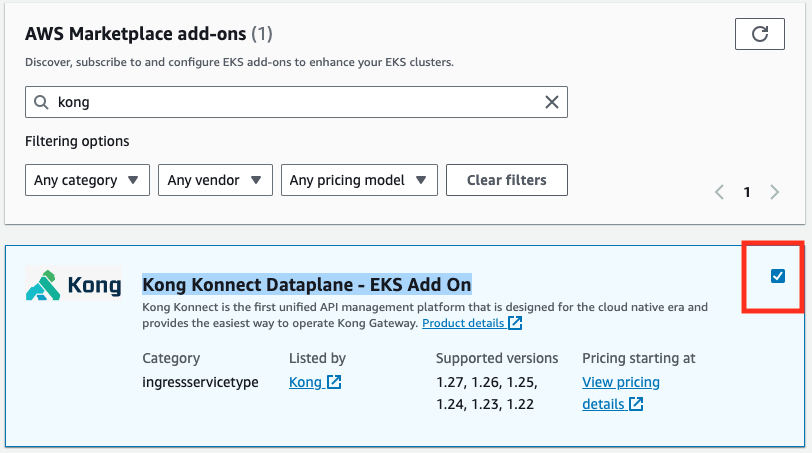
- Under AWS Marketplace add-ons, search, browse or navigate to Kong Konnect Dataplane - EKS Add On , check mark against the result and click Next
- Select the latest default version or any pinned down version of your interest and click Next
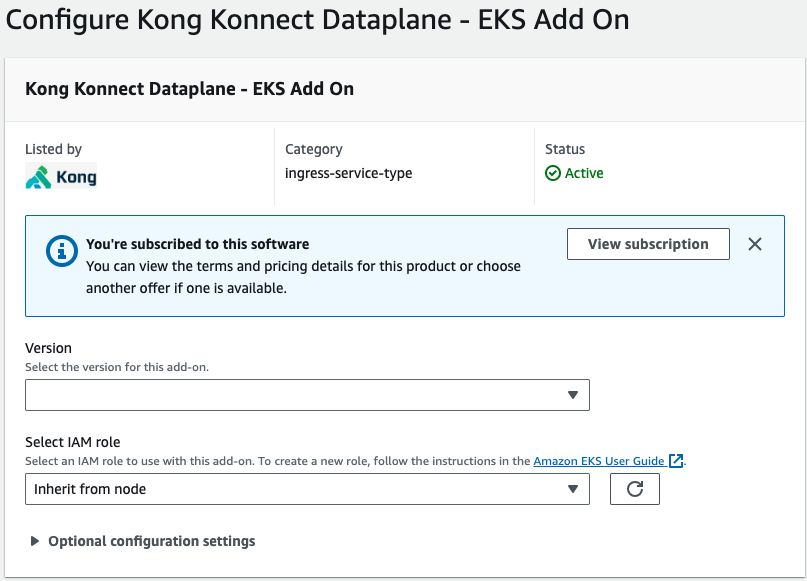
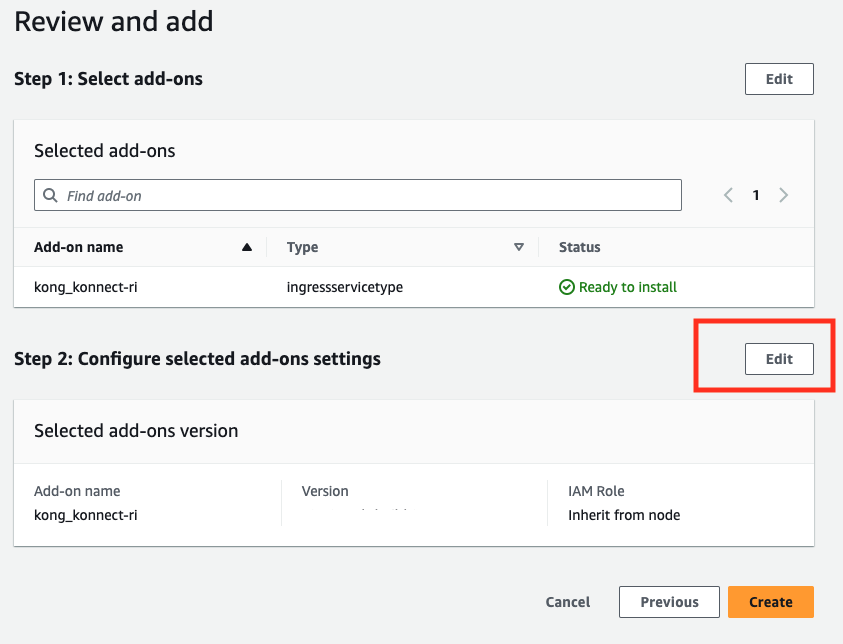
- Under Step 2: Configure selected add-ons settings click Edit
- Under Configuration, paste the values relevant to your Konnect dataplane, follow the example below:
---
env:
cluster_cert: "/etc/secrets/kong-cluster-cert/tls.crt"
cluster_cert_key: "/etc/secrets/kong-cluster-cert/tls.key"
cluster_control_plane: **REPLACE ME**
cluster_server_name: **REPLACE ME**
cluster_telemetry_endpoint: **REPLACE ME**
cluster_telemetry_server_name: **REPLACE ME**
secretVolumes:
- kong-cluster-cert
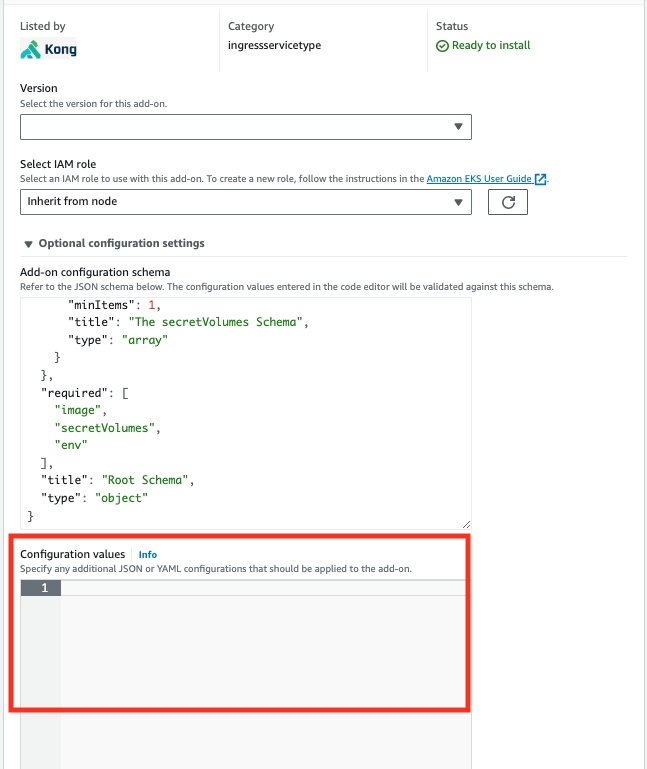
Paste the values as noted in pre-requisite 4.6 above:
cluster_control_planecluster_server_namecluster_telemetry_endpointcluster_telemetry_server_name
- Scroll to the bottom of the page and Click Create
Kong-gratulations. Within a few minutes, you will be able to see the data plane nodes connecting to the specific control plane nodes. You may validate from Kong Konnect UI or by running kubectl get all -n kong
Provision Kong Gateway EKS AddOn via AWS Command Line Interface (CLI)
- Create a configuration file with following values. Save the file as
kong-eks-configuration.yaml
---
env:
cluster_cert: "/etc/secrets/kong-cluster-cert/tls.crt"
cluster_cert_key: "/etc/secrets/kong-cluster-cert/tls.key"
cluster_control_plane: **REPLACE ME**
cluster_server_name: **REPLACE ME**
cluster_telemetry_endpoint: **REPLACE ME**
cluster_telemetry_server_name: **REPLACE ME**
secretVolumes:
- kong-cluster-cert
Paste the values of values of cluster_control_plane, cluster_server_name,cluster_telemetry_endpoint and cluster_telemetry_server_name as noted in pre-requisite 4.6 above
- Execute the following command to install the Kong AddOn
aws eks create-addon --cluster-name REPLACE_ME --region REPLACE_ME --addon-name kong_konnect-ri --configuration-values file://kong-eks-configuration.yaml
where
–cluster-name : Name of your EKS Cluster
–configuration-values : Name and location of the file that you saved at step-1 above
Expected Output
Output will be similar to following
{
"addon": {
"addonName": "kong_konnect-ri",
"clusterName": "konnect-dataplane-graviton",
"status": "CREATING",
"addonVersion": "v3.4.1-eksbuild.0",
"health": {
"issues": []
},
"addonArn": "arn:aws:eks:us-west-2:MASKED:addon/konnect-dataplane-graviton/kong_konnect-ri/62c4cc56-eb56-2cbc-45f2-393fdfc36b70",
"createdAt": "2023-07-27T11:47:57.023000-07:00",
"modifiedAt": "2023-07-27T11:47:57.044000-07:00",
"tags": {},
"configurationValues": "{\n \"env\": {\n \"cluster_cert\": \"/etc/secrets/kong-cluster-cert/tls.crt\",\n \"cluster_cert_key\": \"/etc/secrets/kong-cluster-cert/tls.key\",\n \"cluster_control_plane\": \"6fae8e9e10.us.cp0.konghq.com:443\",\n \"cluster_server_name\": \"6fae8e8f10.us.cp0.konghq.com\",\n \"cluster_telemetry_endpoint\": \"6fae8e9e10.us.tp0.konghq.com:443\",\n \"cluster_telemetry_server_name\": \"6fae8e9e10.us.tp0.konghq.com\"\n },\n \"image\": {\n \"tag\": \"3.4.1.1\"\n },\n \"secretVolumes\": [\"kong-cluster-cert\"]\n}"
}
}
Validation
$ kubectl get all -n kong
NAME READY STATUS RESTARTS AGE
pod/eks-add-on-chart-eks-add-on-chart-6d9cb96cbd-qktwz 1/1 Running 0 23s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/eks-add-on-chart-eks-add-on-chart-proxy LoadBalancer 172.20.55.86 a0d9ed496ade34158ae399c4ffa261c5-215811309.us-west-2.elb.amazonaws.com 80:31767/TCP,443:30065/TCP 23s
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/eks-add-on-chart-eks-add-on-chart 1/1 1 1 23s
NAME DESIRED CURRENT READY AGE
replicaset.apps/eks-add-on-chart-eks-add-on-chart-6d9cb96cbd 1 1 1 23s